Blockchain is a decentralized, immutable database that makes it easier to track assets and record transactions in a corporate network. An asset may be physical (such as a home, car, money, or land) or intangible (intellectual property, patents, copyrights, branding).
On a blockchain network, practically anything of value may be recorded and traded, lowering risk and increasing efficiency for all parties.
1.Importance of a Blockchain
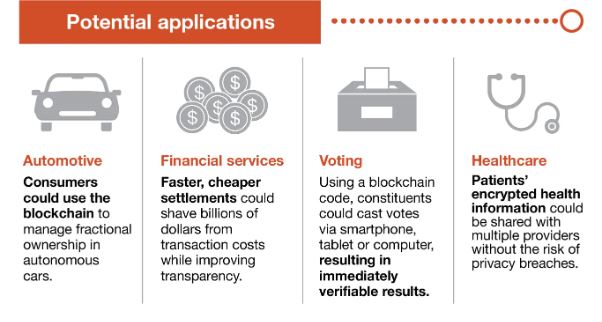
- Blockchain is the best technology for delivering correct information because it offers real-time, shareable, and entirely transparent data that is kept on an immutable ledger and accessible only to members of the permission network.
- Orders, payments, accounts, production, and many other things may all be tracked via a blockchain network.
- Additionally, because everyone has access to the same version of the truth, you can see every aspect of a transaction from beginning to end, increasing your confidence and opening up new prospects.
2. Prominent Features of a Blockchain
- Prevents Duplication: The distributed ledger and its immutable record of transactions are available to all network users. Transactions are only recorded once with this shared ledger, preventing the duplication of effort present in conventional corporate networks.
- Unchangeable records: Once a transaction has been added to the shared ledger, no participant is permitted to alter or interfere with it. A fresh transaction must be added to undo an error in a transaction record before both transactions are displayed.
- Sensible contracts: A set of instructions known as a smart contract is saved on the blockchain and automatically carried out to speed up transactions. A smart contract can specify parameters for corporate bond transfers, stipulate how much must be paid for travel insurance, and much more.
3. Types of Block Chain
For compliance and regulatory reasons, private and permissioned networks are ideal. Public and permissionless networks, on the other hand, can achieve more decentralization and diffusion.
- Public blockchains are open to the public, and anybody can join and validate transactions on them.
- Private blockchains are mainly restricted to commercial networks. Membership is controlled by a single entity, or consortium.
- Processors are not restricted in permissionless blockchains.
- Permissioned blockchains are only accessible to a specific group of users who have been issued identities via certificates.
4. Key Elements of Blockchain
- Magic Number: A number with specific values known as a “magic number” designates a block as belonging to a given cryptocurrency’s network.
- Blocksize: Limits the amount of data that can be written into a block by defining its maximum size.
- Block Header: Information about the block is contained in the block header.
- Transaction counter: A statistic that indicates how many transactions are contained in a block is known as a transaction counter.
- Transactions: A list of all the transactions contained in a block is called a transaction.
5. Exploitation on Block Chain
- Phishing Attacks
Phishing is an effort to get a user’s login information through fraud. Owners of wallet keys receive emails from scammers that appear to be from a reliable source. The emails contain bogus hyperlinks that request users’ login information. The blockchain network and the user may both suffer damages if someone gains access to a user’s credentials and other sensitive information.
- Routing Attacks
Real-time, massive data transfers are essential for blockchains. Data that is being transferred to internet service providers can be intercepted by hackers. In a routing attack, blockchain participants seems everything appear to be normal. However, while behind scammers have taken money or private information.
- 51% Attacks
A significant amount of computational power is needed for mining, particularly for massive public blockchains. However, if a miner or a group of miners could pool enough funds, they might have more than 50% of the mining power of a blockchain network. Having control over the ledger and the ability to influence it requires having more than 50% of the power.
6. Bitcoin and Block Chain
The Bitcoin protocol is constructed on blockchain . It’s important to note that blockchain is only employed by Bitcoin to immutably record a ledger of payments in a transparent manner. In theory blockchain could be used to immutably record any number of data points
7. Pros and Cons of Block chain
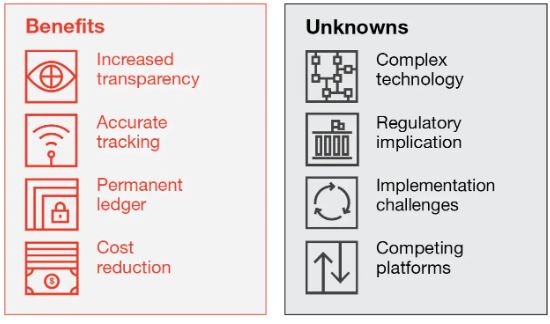
- Increased accuracy due to the absence of human verificationIncreased accuracy due to the absence of human verification.
- Cost savings through the abolition of third-party verification
- Decentralization makes it more difficult to interfere
- The transactions are efficient, confidential, and safe.
- Open-source technology
- Gives residents of nations with unstable or weak governments a financial alternative and a way to secure their personal information.
Cons :
- Bitcoin mining has a high technological cost.
- Low transactional speeds
- Use in illegal operations in the past, such as on the dark web
- Regulation differs between jurisdictions and is still ambiguous.
- Storage restrictions for data.
8. How Blockchain Works
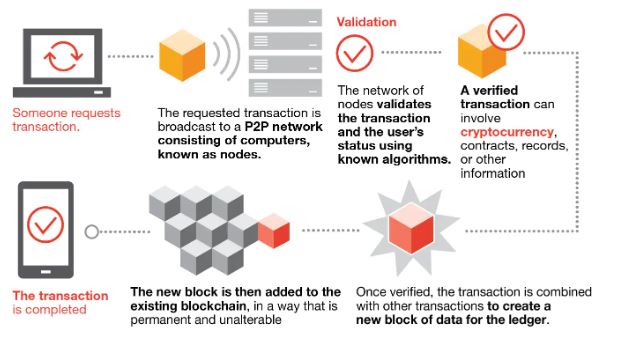
- Blockchain is a decentralized, immutable database that makes it easier to track assets and record transactions in a corporate network.
- An asset may be physical (such as a home, car, money, or land) or intangible (intellectual property, patents, copyrights, branding). Public and permissionless blockchains achieve more decentralization and diffusion.
- Public blockchains are open to the public, and anybody can join and validate transactions on them. Phishing is an effort to get a user’s login information through fraud.
- The blockchain network and the user may both suffer damages if someone gains access to user’s credentials. The Bitcoin protocol is constructed on a public ledger of transactions called a block chain.
- Blockchains are essential for real-time, massive data transfers to internet service providers. Data that is being transferred to internet providers can be intercepted by hackers in a routing attack.

